Heap spraying in information security is an attack that uses errors in working with the application's memory . Attacking with heap spraying, a hacker forces the application to allocate memory for a large number of objects containing malicious code . This increases the likelihood of success of the exploit, which transfers the flow of execution to a certain position within the heap . It is important to understand that without an exploit that allows you to change the flow of execution, heap spraying will not cause any harm. The attack is based on the predictability of the position of the heap in the address space of the process . In addition, heap memory allocation is a deterministic operation that makes it possible to successfully apply this technique. Heap spraying is especially effective in browsers where a hacker can allocate memory using a few lines of javascript on a web page . An important role is played by the similarity of memory allocation in different operating systems , which makes this attack cross-platform. As a result, you can add a certain sequence of bytes (for example, a machine instruction) to a pre-predicted address in the memory of the target process [1] .
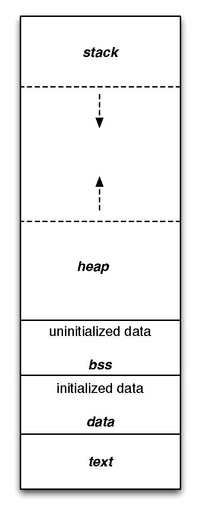
When creating a process in the operating system , the address space [2] [3] [4] is allocated for its needs, in which user data, executable code and some system information that depends on the specific operating system are located. User data is distributed between the heap and the stack, depending on the method of allocating memory for them [5] . For example, variables with an automatic allocation class are stored in the stack segment, as well as information that is saved with each function call, for example, static variables and the return address when a function is called . A heap is a region of dynamic memory , that is, when dynamically allocating memory, space is allocated on the heap. Traditionally, the heap and stack grow towards each other [2] [3] [4] .
Content
Basic concept
Heap spraying by itself is not a vulnerability . However, it can be used to deliver malicious code to the executable area of the process . This technique uses the determinism of the memory allocation operation in the system . This means that a large amount of memory is often located with the same offset in the address space of the process. However, this technique is not able to create a gap in the security system itself. Therefore, its use requires a vulnerability that allows you to change the order of execution of commands (machine instructions) [6] .
It is difficult to use this technique, since there are a large number of factors influencing the execution of the process (from the hacker's point of view). However, with the help of heap spraying, a large number of instructions can be executed, which partially compensates for this difficulty and increases the probability of a successful hack [7] .
Heap spraying can be implemented for most operating systems and architectures . The main difficulty is finding a vulnerability that allows you to redirect the flow of execution . Dynamic allocation of a large amount of memory, as mentioned earlier, is an operation that allows you to predict the position of a heap in memory (at the moment of virtual memory projection ) [8] . Each time performing the same sequence of memory accesses, the heap will most likely end up in the same place [6] [7] .
However, in order to increase this probability, it is necessary that the size of the piece of memory allocated is comparable to the size of a segment or page , depending on how the memory is organized [7] .
The main problem of this attack is a change in the flow of execution . Without the ability to intercept the execution of this type of attack does not make sense. Some functions may store the return address on the heap, then the hacker may try to change them. In this case, when returning from such a function, a move will occur to the memory location convenient for the hacker , and, as a result, the malicious code will be executed. Any function that reads the address on the heap can be used as a vulnerability. The hacker can replace this address with the address of the memory section modified by him. This can lead to redirection of the execution flow to the malicious code. However, this is not as simple as it seems [1] [8] .
The correctness of the address (its size, offset from the beginning of the page) used for the substitution is highly dependent on the architecture. Therefore, in practice they use blocks consisting mainly of NOPs , appending the necessary code at the end. This technique allows you to not worry about the accuracy of the calculation of the address and direct the flow of execution to an approximate place in the address space [1] .
Steps to implement heap spraying:
- Determining the size of a piece of allocated memory so that one selection matches the size of the page.
- Selection of several pieces in which the NOP and the shell code are located .
- Using a known vulnerability to redirect the command counter to the intended position of the pieces, for example, using a stack overflow .
- Execution of the selected area [1] [6] .
This type of attack is very effective in browsers . Most browsers support the execution of scripts . A hacker can allocate the necessary memory using a few lines of JavaScript or ActionScript on a web page. An important role is played by the similarity of memory allocation in different operating systems , which makes this attack cross-platform. Moreover, the addresses that need to make the transition will be similar [9] .
History
The first time heap spraying was used in 2001 and became widespread in the summer of 2005. After a large number of vulnerabilities were found in Internet Explorer [10] [11] . The exploits were very similar to each other. Each such exploit consisted of heap spraying, the method of implementation of which did not change, and the transfer of the instruction counter to the required place in memory . Therefore, a new exploit was obtained by changing several lines of HTML and switching to a new vulnerability [1] .
Implementation
Javascript
The easiest way to allocate space in the browser's memory is to declare a string variable and initialize it [1] .
Examples of memory allocation in JavaScript [9] :
var myvar = "CORELAN!" ;
var myvar2 = new String ( "CORELAN!" );
var myvar3 = myvar + myvar2 ;
var myvar4 = myvar3 . substring ( 0 , 8 );
These are very simple examples, since the highlighted lines are small. A piece of shell code is much larger, but still smaller than a whole page of memory .
Hypothetically, it is possible to write the necessary shell code many times into each block we allocate, but then the attacker will have to keep track of what specific address the pointer falls in, since it should not fall in the middle of the executable code . Usually they do it differently - they pick out pieces containing many NOPs , and in the end write the necessary commands. Then, due to the linearity of the arrangement of the blocks in the heap, it is easier to observe the linearity of the execution of the code and there is no need to worry about the accuracy of hitting the beginning of a piece of memory [9] .
With the right size, the allocated chunks of memory should be very close to the size of the heap item. If the allocated piece of memory is smaller, the remaining space will be free. The memory manager will , at best, leave system garbage in this “unallocated space”, and at worst put an object that fits in size. In any case, this will lead to an error when trying to execute this memory location [1] [9] .
Thus, the script used by hackers looks like this [9] :
< html >
< script >
var shellcode = unescape ( '% u \ 4141% u \ 4141' ); // this is the inscription CORELAN
var bigblock = unescape ( '% u \ 9090% u \ 9090' ); // 90 is the NOP code
var headersize = 20 ;
var slackspace = headersize + shellcode . length ; // initial size of our piece: useful code + header size
while ( bigblock . length < slackspace ) bigblock + = bigblock ; // fill with NOPs
var fillblock = bigblock . substring ( 0 , slackspace ); // useful code filling
var block = bigblock . substring ( 0 , bigblock . length - slackspace ); // just NOPs
while ( block . length + slackspace < 0x40000 ) block = block + block + fillblock ;
// Fill to the size of the heap element - in this case it is 0x40000
var memory = new Array ();
for ( i = 0 ; i < 500 ; i ++ ) { memory [ i ] = block + shellcode } // selection of several such elements.
</ script >
</ html >
unescape() is a function that allows you to put the bytes in exactly the order in which indicated in the argument [1] .
VBScript
VBScript is used in Internet Explorer to create strings using string . Conceptually, it does not differ from the implementation in JavaScript , only the names of the functions change [6] .
ActionScript
In July 2009, exploits were found that allow using ActionScript to implement heap spraying in Adobe Flash [1] .
HTML5
In September 2012, a new implementation was introduced at EuSecWest 2012 [12] . Federico Muttis and Anibal Sacco showed that heap spraying with a high degree of granularity can be implemented using HTML5 technologies. They used the low-level raster interface provided by the canvas API .
Images
There are methods that use image loading. The image is made up of NOPs and then acts as in the previous cases [1] [9] .
Prevention Methods
As with any buffer overflows , there are three main protection paths. [1] It is often easier to prevent a change in the flow of execution than using the buffer itself. Modern operating systems use all of the following methods:
- Prevent execution by separating data and executable code , usually using architectural solutions, such as NX bit . For example, DEP has already been implemented in most OS [1]
- Increased randomness of data in memory . For example, so that the next selected element of the heap does not have a fixed offset relative to the current one. Already implemented in most operating systems: ASLR [7] .
- Increasing the number of checks for compliance with buffer boundaries in the memory manager
Projects associated with this type of attack:
- Microsoft Research's Nozzle project aims to prevent heap spraying [1] .
- BuBBle is another project whose goal is to minimize the damage from this attack [13] .
See also
- Buffer overflow
- Stack overflow
- Call stack
- Heap (memory)
- Hacker attack
- Data Execution Prevention
Notes
- ↑ 1 2 3 4 5 6 7 8 9 10 11 12 13 Benjamin Livshits, Paruj Ratanaworabhan, Benjamin Zorn. NOZZLE: A Defense Against Heap-spraying Code Injection Attacks. (English) : Inproceedings. - 2009. - p . 38 .
- ↑ 1 2 Tanenbaum E., Woodhull A. Operating Systems. Design and implementation. - SPb. : Peter, 2007. - p. 78-252. - 704 s.
- 2 1 2 Richter J. Windows for professionals: creating efficient Win32 applications tailored to the 64-bit version of Windows. - Moscow : Russian Edition, 2008. - p. 68-118,333-418. - 720 s.
- ↑ 1 2 W. Richard Stevens, Stephen A. Rago. UNIX. Professional programming. - SPb. : Symbol Plus, 2014. - p. 288-351. - 1104 s.
- ↑ Brian Kernighan, Dennis Ritchie. C programming language. - Williams, 2015. - p. 93-123. - 304 s.
- ↑ 1 2 3 4 Thomas Toth, Christopher Kruegel. Accurate buffer overflow detection via English payload execution (English) // RAID'02 - 2002. - 16 October. - p . 274-291 . - ISBN 3-540-00020-8 .
- ↑ 1 2 3 4 Tilo Muller. ASLR Smack & Laugh Reference (English) . - 2008. - 17 December. - p . 21 .
- ↑ 1 2 Mark Russinovich, David Solomon. Windows internal device. - SPb. : Peter, 2013. - p. 104-681. - 800 s.
- ↑ 1 2 3 4 5 6 Sotirov A. Heap feng shui in javascript (eng.) . - 2007. - p . 55 .
- ↑ HwaiGeeng, Chew. Security Holes in ISAPI Extensions (English) : Inproceedings. - 2001. - p . 12 .
- ↑ Black Hat. Security Holes in ISAPI Extensions (English) : Inproceedings. - 2010. - p . 35 .
- ↑ Anibal Sacco, Federico Muttis. HTML5 Heap Sprays, Pwn All The Things (English) . - 2012.
- ↑ Francesco Gadaleta, Yves Younan, Wouter Joosen. BuBBle: A Javascript Engine Level Countermeasure against Heap-Spraying Attacks (eng.) . - 2010. - p . 17 .
Literature
- Richter J. Windows for professionals: creating effective Win32 applications tailored to the 64-bit version of Windows. - Moscow : Russian Edition, 2008. - p. 68-118,333-418. - 720 s.
- W. Richard Stevens, Stephen A. Rago. UNIX. Professional programming. - SPb. : Symbol Plus, 2014. - p. 288-351. - 1104 s.
- Tanenbaum E., Woodhall A. Operating Systems. Design and implementation. - SPb. : Peter, 2007. - p. 78-252. - 704 s.
- Brian Kernigan, Dennis Ritchie. C programming language. - Williams, 2015. - p. 93-123. - 304 s.
- Mark Russinovich, David Solomon. Windows internal device. - SPb. : Peter, 2013. - p. 104-681. - 800 s.
Links
- Exploit Writing Tutorial (English) . Corelan Team. The appeal date is December 12, 2015.
- Fundamentals of Garbage Collection (eng.) . Msdn The appeal date is December 12, 2015.
- Running processes using exec () call . Opennet. The appeal date is December 12, 2015.
- Hungpages (English) . Debian. The appeal date is December 12, 2015.
- ActionScript Heap Spray (eng.) . Julia Wolf. The appeal date is December 12, 2015.
- HTML5 Heap Spray (eng.) . EUSecWest 2012. Appealed on December 12, 2015.
- Address Space Layout Randomization (ASLR) (English) . CISCO. The appeal date is December 12, 2015.