Triple DES (3DES) is a symmetric block cipher created by Whitfield Diffie , Martin Hellman and Walt Tachmann in 1978 on the basis of the DES algorithm in order to eliminate the main shortcoming of the latter - a small key length (56 bits), which can be cracked by the method of complete enumeration of the key. The speed of 3DES is 3 times lower than that of DES, but the cryptographic strength is much higher - the time required for 3DES cryptanalysis can be a billion times longer than the time required to open DES. 3DES is used more often than DES, which is easily cracked using today's technologies (in 1998, the Electronic Frontier Foundation , using a special DES Cracker computer, opened DES in 3 days). 3DES is an easy way to fix DES. The 3DES algorithm is built on the basis of DES, so it is possible to use programs created for DES to implement it. The official name of the algorithm used in the standards is TDEA or Triple DEA (English Triple Data Encryption Algorithm). However, the term “3DES” is used more generally by providers, users, and cryptosystem developers.
| Triple DES | |
|---|---|
 | |
| Creator | Ibm |
| Published | 1978 |
| Key size | 112 (2TDES) or 168 bits (3TDES) |
| Block size | 64 bit |
| Number of rounds | 48 DES equivalent rounds |
| Type of | Feistel Network |
Content
- 1 Algorithm
- 2 Key selection
- 3 Encryption of more than one block
- 4 Cryptographic strength
- 5 3DES Application
- 6 References
- 7 See also
- 8 Notes
Algorithm
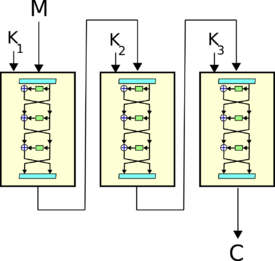
The diagram of the 3DES algorithm is as shown in the figure. A simple version of 3DES can be represented as follows:
Where , , - keys for each DES step, - input data to be encrypted. There are 3 types of 3DES algorithm:
- DES-EEE3 : Encrypted three times with three different keys (encryption-encryption-encryption operations).
- Encryption:
- Decryption:
- DES-EDE3 : 3DES encryption-decryption-encryption operations with three different keys.
- Encryption:
- Decryption:
- DES-EEE2 and DES-EDE2 : Like the previous ones, except that the same key is used in the first and third steps.
- Encryption:
- Decryption:
The most popular version of 3DES is DES-EDE3.
Key Selection
When executing the 3DES algorithm, keys can be selected as follows:
- , , are independent.
- , independent and
The safest is the first option: the DES key is 56 bits long, and the 3DES is 3 times longer, that is 168 bits (each byte of a 64-bit DES key uses only 7 bits, so in fact the key length is 56 bits, not 64, and the 3DES key length is 168, not 192 bits).
The second option is somewhat less persistent, with a key length of 2 × 56 = 112 bits. However, this encryption option is more reliable than conventional double-encryption with DES with keys. and : it protects the “ meeting in the middle ” attacks.
The third option is equivalent in DES reliability: here the key length is also 56 bits. When using the DES-EDE3 algorithm, due to this choice of keys, encryption (first step) and decryption (second step) nullify each other. This selection of keys is now no longer recommended by the National Institute of Standards and Technology (NIST) [1] and is not supported by the ISO / IEC 18033-3 standard.
Each DES key is stored and transmitted as 8 bytes, each byte with odd parity [2] , so a complete set of keys will occupy 24 bytes in the first embodiment, 16 in the second and 8 in the third.
Encryption of more than one block
As with other block ciphers, encryption and decryption of several data blocks can be performed using one of the encryption modes , which are determined independently of the block encryption algorithm itself. However, ANSI X9.52 indicates directly, and NIST SP 800-67, through SP 800-38A [3] , that some modes can be used only with certain restrictions that are not necessary in the general case. For example, ANSI X9.52 clarifies that for the ciphertext block interlocking mode, the initialization vector must change each time, while ISO / IEC 10116 [4] does not require this. FIPS PUB 46-3 and ISO / IEC 18033-3 define 3DES for only one block and do not impose any restrictions on the encryption modes of several blocks. Despite the fact that the ciphertext block coupling mode (Triple CBC) improves the strength of the cipher, the electronic codebook (Triple ECB) mode is currently more common.
Cryptographic Strength
3DES with three different keys has a key length of 168 bits, but due to the “ meeting in the middle ” attacks, the effective cryptographic strength is only 112 bits. In the version DES-EDE c the nominal key size is also 112 bits. However, this choice of keys is vulnerable to certain plaintext attacks , which reduces the effective key length to 80 bits. A successful 3DES attack will take about a bit of famous plaintext steps DES encryption cycles and memory bit [5] . This is not practical at the moment, and according to NIST estimates, an algorithm with three different keys should remain reliable until the 2030s.
3DES Application
Three-key 3DES is implemented in many Internet- oriented applications, including PGP and S / mime. Triple DES is a fairly popular alternative to DES and is used for key management in ANSI X9.17 and ISO 8732 and in PEM (Privacy Enhanced Mail). The electronic payment industry uses 3DES and continues to actively develop and publish standards based on it (for example, EMV ). Microsoft OneNote , Microsoft Outlook 2007, and Microsoft System Center Configuration Manager 2012 use 3DES to protect system and user data with passwords. Known cryptographic attacks that are applicable in practice on 3DES do not exist.
Nevertheless, 3DES is gradually becoming obsolete: it is being replaced by a new AES Rijndael algorithm . Rijndael, software implemented, is up to six times faster. Therefore, 3DES is more suitable for hardware implementations. Many security systems continue to support both 3DES and AES, using AES by default. Although 3DES may be supported for backward compatibility, it is no longer recommended.
Links
- 3DES using CryptoAPI and .NET
- Triple DES
See also
- DESX
- DES
Notes
- ↑ Special Edition of NIST 800-67 Revision 1: Recommendation for the Triple Data Encryption Algorithm (TDEA) Block Cipher , 2012 .
- ↑ ANSI X3.92-1981 (one of the standards defining DES), section 3.5: "One bit in each 8-bit byte of the KEY may be utilized for error detection in key generation, distribution, and storage. Bits 8, 16 , ..., 64 are for use in ensuring that each byte is of odd parity. "
- ↑ Special Edition of NIST 800-38A, Recommendation for Block Cipher Modes of Operation, Methods and Techniques , 2001 (PDF)
- ↑ ISO / IEC 10116: 2006 Information technology - Security techniques - Modes of operation for an n-bit block cipher
- ↑ Stefan Lucks : Attacking Triple Encryption Archived on November 9, 2005. ( PDF ), Fast Software Encryption 1998, pp. 239–253.